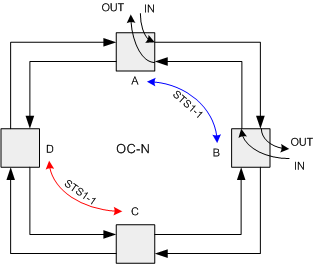
A
ring is defined as a set of nodes interconnected to form a closed loop, where
fiber cables
the
traffic is added and where it is dropped, see figure 1.

Figure
1.
This
is much different than the UPSR where traffic between any two nodes consumes
bandwidth on the entire. Again
referring to figure 1. we see that if an STS-1 is provisioned between nodes A
and B on time slot 1 that time slot will also be available for use between nodes
C and D, (STS1-1, STS-1 number1). This
flexibility in the reuse of bandwidth is one of the major advantages of a BLSR.
The price you pay for this flexibility as a user is greatly increased
complexity in provisioning and troubleshooting.
Protection against fiber cuts and node failures is done by reserving
bandwidth on the ring strictly for protection.
In the BLSR OC-N network of figure 1. exactly one half of the bandwidth,
N/2 is available for working traffic between adjacent nodes.
The other N/2 of bandwidth is reserved for protection. In an OC-48 system time slots 1-24 are used for working
traffic and 25-48 are reserved for protection.
At first glance this would seem to be a waste of 1/2 of the system
bandwidth. Upon closer examination
it can be seen that this is not the case. Figure
2 illustrates this fact. Twentyfour
STS-1s are provisioned between node A and B node A’s East span and 24 STS-1s
are provisioned between node A and node C on node A’s West span.
Notice that node D is just a pass through node with no traffic being
added or dropped. In fact it would be impossible to add/drop and traffic at
node D because the maximum allowed bandwidth, N/2, is allocated as pass through
traffic. In this example of an
OC-48 ring 48 STS-1s (ring line rate) have been provisioned and there is no more
bandwidth left on the ring. This is
reminiscent of the UPSR case. In
fact in a hubbing scenario the capacity of a BLSR and UPSR are identical and
equal to the ring line rate, N.
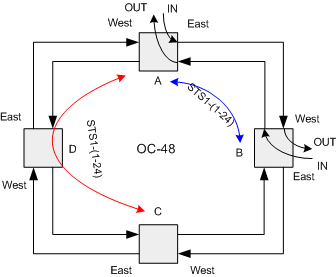
Figure 2.
If
traffic is not hubbed the BLSR can have a significant capacity advantage over
the UPSR. The extreme case of this
is when all traffic is between adjacent nodes.
Figure 3 illustrates this graphically.
The capacity advantage here is 2 times that of a UPSR, or 96.
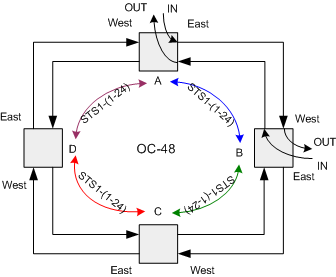
Figure
3.
For the case of adjacent node traffic the capacity advantage of the BLSR grows linearly with the number of nodes, however in most cases the traffic will likely resemble a distributed logical mesh still providing a capacity advantage but not quite as extreme as in the adjacent node traffic case.
Protection
Switching in The BLSR
To
illustrate the protection switching in a BLSR assume the traffic patter shown in
figure 4. STS-1 number 1 from node
A via short path to node B and STS-1 number 2 from node A to node C via pass
through node B.
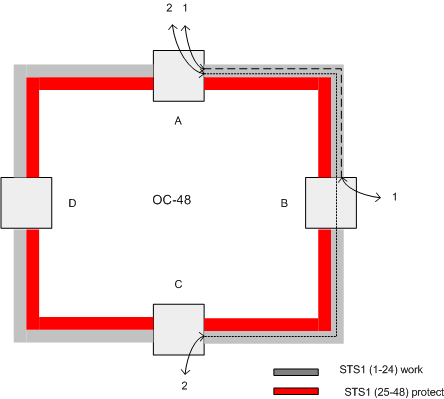
Figure 4.
When
a cable cut occurs as shown in
figure 5, both nodes adjacent to the cut detect an
LOS and
In
order to perform a ring switch, the protection channels are essentially shared
among each
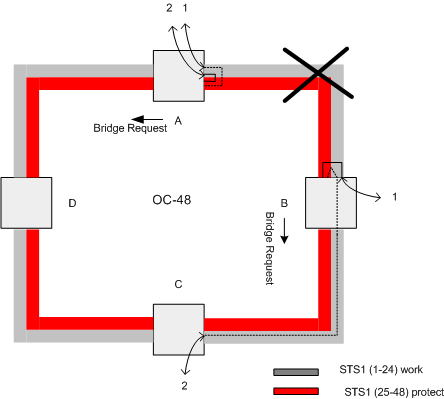
Figure
5.
Extra
Traffic
During
fault-free conditions, it is possible to use the protection channels to carry
additional